8 Most Effective Open Source Penetration Testing Tools
Open source penetration testing tools offer a powerful and cost-effective way to assess
the network security and to remediate the revealed vulnerabilities.
Is it possible to know how vulnerable your project is? It is worth use some of the spread open source penetration testing instruments that are widely used by white hackers around the world, as they assist to figure out holes in safety and fix them in timely manner.
Want to have an in-depth understanding of all modern aspects of Open Source Penetration Testing Tools? Read carefully this article and bookmark it to get back later, we regularly update this page.
Free DemoWhat Is Open Source Penetration Testing?
With the change in the way computer systems are used and built, security means a lot. While companies realize that they can't secure every system by 100%, it is imperative for them to know exactly what security challenges they may face. Open source penetration testing provides organizations with an understanding of their real security situation.
Want to have an in-depth understanding of all modern aspects of Open source Penetration Testing? Read carefully this article and bookmark it to get back later, we regularly update this page.
Open source penetration testing is no less than a fine way to assess the security of an information system by simulating targeted attacks using open source intelligence (OSINT) platforms and tools. Such penetration test will make it possible to assess the security of an information system against unauthorized attacks using various intrusion models. The main purpose of the test is to identify the main weaknesses, the most successful attack patterns and the possible amount of damage.
So open source penetration testing makes it possible to check web servers, DNS servers, router settings, analyze vulnerabilities of workstations, check the ability to access critical information, check remote access systems, opened ports, properties of available services and everything else that a real hacker can use to get unauthorized access to protected information assets of the organization.
| ImmuniWeb® Discovery reduces complexity and costs of cybersecurity compliance via continuous discovery of your external digital assets and attack surface enhanced with proactive dark web monitoring. Learn more with ImmuniWeb Discovery |  |
Operating Systems for Open Source Penetration Testing
Regardless of whether you are working as a security professional or just interested in this topic, you need to choose one of the operating systems sharpened for open source penetration testing. Today such operating systems are indisputably a must for anyone doing ethical hacking, whether professional or non-professional. To do this, it is worth knowing at least a couple of decent Linux distributions that are used in most cases for this. Some of the more popular ones are:
Kali Linux
Kali Linux operating system is based on Debian and is considered one of the best and foremost for the purposes of ethical hacking and penetration testing.
Backbox Linux
Backbox Linux uses the Ubuntu Linux OS and is among the top popular operating systems for White Hat hacker penetration testing.
Black Arch
Black Arch based on Arch Linux. It is a lightweight operating system for professional ethical hackers who can skillfully work with Linux. Black Arch includes a huge number of tools and thousands of hacking tools.
Parrot Security
Parrot Security is also considered one of the best systems of its kind for open source penetration testing purposes as well as forensics, which is suitable for both novice and expert. The platform has a wide variety of great hacking tools in the repository.
Network Security Toolkit (NST)
Network Security Toolkit or as it is commonly called NST, which is based on Fedora. It is the operating system mostly for ethical hacking professionals for open source penetration testing. In addition, the distribution is often used for network penetration operations to ensure its protection. The Network Security Toolkit contains the most used professional tools for network penetration test purposes.
| ImmuniWeb Community Edition is a collection of free security tests for any occasion. You can test your cloud storage, email servers, website, mobile apps, SSL security and even run a dark web exposure test. Learn more with ImmuniWeb Community Edition | 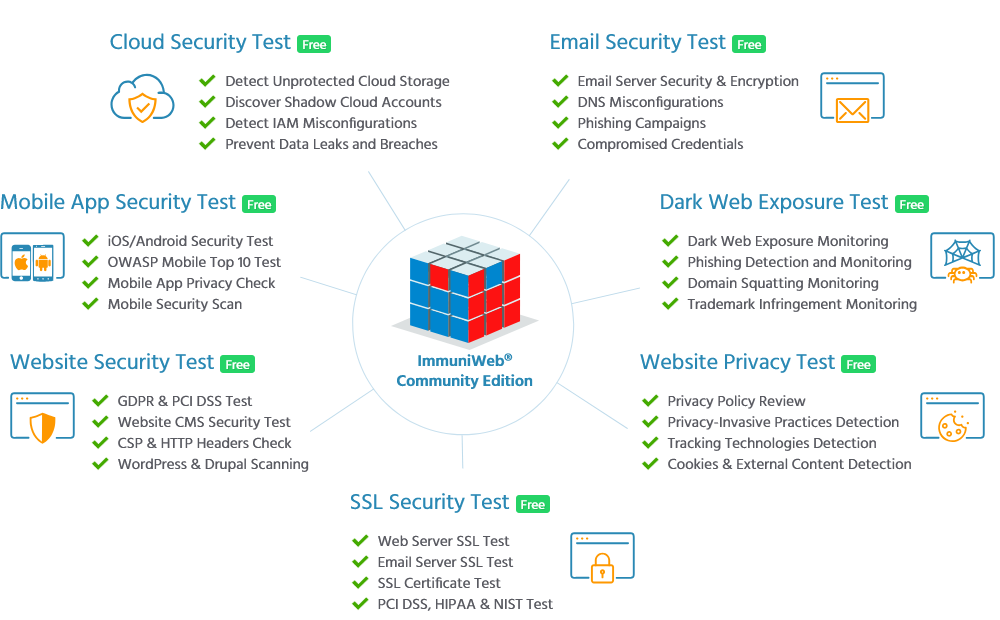 |
Open Source Penetration Testing Tools
There are various open source systems and programs for penetration testing and finding weaknesses in the IT infrastructure of organizations, which include various categories: complex tools, brute-forcing, network scanners and traffic analyzers. Some of these tools are preinstalled in Kali Linux, others can be downloaded separately.
Comprehensive tools for open source penetration testing are applications that are characterized by broad functionality and provide a comprehensive check for possible vulnerabilities. Here are our list of eight widely spread and most effective ones:
1. OWASP ZAP
A cross-platform open source penetration testing tool liked by security pros around the world. The OWASP ZAP interface consists of several windows and is easy to use. The app mechanically indicates weak points in security in web applications while they are developing and testing. This instrument supports a dozen languages, so the program will be useful not only for pentesters, but also for web developers themselves.
2. Burp Suite
Burp Suite is a popular web application security testing platform that is available on Kali Linux out of the box. In essence, it is a set of interconnected components that provide a complete security audit. The functionality goes beyond searching for files, displaying application content, guessing passwords, fuzzing, intercepting and modifying requests, but offers a wide range of possibilities. In the BApp Store you can choose one of the three available plans, as well as find additional extensions for Burp Suite that can increase the functionality of the program.
3. Metasploit
Metasploit for penetration testing framework is a popular open source penetration testing platform for creating and debugging exploits for various operating systems. We can say that today it is the most advanced and popular framework that can be used for penetration testing. It is based on the concept of an "exploit", which is code that can transcend security measures and enter a specific system.
Metasploit runs the "payload" code that performs operations on the target machine, creating an ideal penetration testing environment. Framework Includes a huge code base and allows you to hide attacks from IDS / IPS systems. Thanks to this, testing for vulnerabilities is as close as possible to real scenarios.
The Metasploit platform can be used in web apps, networks, servers, and so on. The program has a command line and graphical interface and runs on Linux, Microsoft Windows, and Apple Mac OS X. Today, the tool has about 800 contributors, and their number constantly increasing. The Metasploit Framework runs on Windows, Linux, and other UNIX-like systems. The trial version of Metasploit has some limitations as it is a commercial product.
Brute-forcers for open source penetration testing help to get unauthorized access to accounts, websites, computer systems by brute-forcing combinations of various characters. Some people think that brute force is outdated, but in fact, this type of hacking is relevant, since the number of brute force attacks has only increased with the transfer of the whole world to a remote mode of operation.
4. RainbowCrack
RainbowCrack is a popular hash cracker that is characterized by high speed of operation. It differs from many brute-force attacks in the way of cracking: instead of a brute force enumeration of combinations with the calculation and comparison of the hash with the desired value, RainbowCrack compares the hash with the values from the pre-calculated table. That is, time is spent only on the comparison, which contributes to a quick result. On the official website of the program, you can find the demo and ready-made rainbow tables for hashing algorithms LM, NTLM, MD5, and SHA1.
5. THC-Hydra
THC-Hydra is an easy-to-use multifunctional password brute-force that has gained popularity among pentesters around the world. Hydra supports a wide range of services, is fast, reliable, and open source. Works through a command line interface using dictionaries.
6. John the Ripper
John the Ripper is an open source cross-platform tool that is used to audit weak passwords. Despite such a flashy name, John the Ripper has established himself well in the field of penetration testing. The program immediately supports such attack options as dictionary brute force, full brute force and hybrid attacks. John the Ripper has a user-friendly Johnny GUI that is installed separately. But Linux owners will have to either build it from the source themselves or be content with the console.
7. W3af
W3af (Web Application Attack Framework) is a powerful open source web application security scanner that can be used to identify and exploit vulnerabilities in web applications. It is designed to be flexible and customizable, allowing security professionals to tailor their scans to their specific needs.
8. Fiddler
Fiddler is a web debugging proxy that captures HTTP(S) traffic between your computer and the internet. It acts as a man-in-the-middle, intercepting and analyzing all network traffic. This tool is invaluable for developers and security professionals who need to understand how web applications work and identify potential vulnerabilities.
| ImmuniWeb Community Edition is a collection of free security tests for any occasion. You can test your cloud storage, email servers, website, mobile apps, SSL security and even run a dark web exposure test. Learn more with ImmuniWeb Community Edition |  |
How to Choose the Right Open Source Pentesting Tool
Choosing the right open-source penetration testing tool depends on your specific needs and expertise. Here are some factors to consider:
Purpose
Network Scanning
Tools like Nmap and Nessus are excellent for discovering hosts, services, and vulnerabilities on a network.
Web Application Testing
Burp Suite, OWASP ZAP, and W3af are designed specifically for web application security testing.
Password Cracking
John the Ripper and Hydra are powerful password cracking tools.
Wireless Network Auditing
Aircrack-ng is a popular choice for wireless network analysis and cracking.
Features
Functionality
Consider the specific features you need, such as vulnerability scanning, exploitation, reporting, and automation.
Customization
Some tools offer more customization options than others, allowing you to tailor them to your specific requirements.
Plugins and Extensions
Check if the tool has a community of developers who create plugins and extensions to extend its functionality.
Ease of Use
Interface
Consider the user interface and how easy it is to navigate and use the tool.
Documentation
Good documentation can help you learn how to use the tool effectively.
Community Support
A strong community can provide support and resources for learning and troubleshooting.
Learning Curve
Complexity
Some tools are more complex than others, so consider your level of technical expertise.
Tutorials and Resources
Look for tools with plenty of tutorials and resources available online.
Compatibility
Operating System
Ensure the tool is compatible with your operating system.
Target Systems
Consider the types of systems you need to test, such as web applications, servers, or networks.
| ImmuniWeb Community Edition is a collection of free security tests for any occasion. You can test your cloud storage, email servers, website, mobile apps, SSL security and even run a dark web exposure test. Learn more with ImmuniWeb Community Edition |  |
Manage Your Vulnerabilities
Organizations' infrastructure consists of dozens, if not hundreds, of different hardware with their own operating systems and applications. Maintaining an acceptable level of information security, when dozens of new vulnerabilities appear every day, has become an urgent problem for security departments in every organization. Almost every IT infrastructure has vulnerabilities, which are usually closed by all kinds of software updates.
Traditional firewalls fail to protect Web resources from most threats. The reason is that such attacks most often occur at the application level, in the form of standard requests to the Web resource, where the capabilities of the firewall are extremely limited and it is not able to detect this attack.
| For such purposes, it is worth using ImmuniWeb Continuous penetration testing, which provides constant monitoring at the required level and has a large number of signatures to control your web applications and APIs. Learn more about ImmuniWeb Continuous |  |
Using these vulnerabilities, hackers carry out an attack on important IT objects of the organization, therefore, it is necessary to identify and close these vulnerabilities in a timely manner. Using vulnerability scanners, you can get an up-to-date picture of existing problems in the network and promptly fix them. Using external scanning, you can check the network perimeter for vulnerabilities. Scans and updates must be carried out at regular intervals to avoid significant "holes" in information systems.
Specialists perform scans such as internal network and software scanning, external network perimeter scanning, and web resource scanning. Vulnerability Scanning provides identification of vulnerabilities in the IT infrastructure of an organization and, as a result, shows weaknesses, after which recommendations are provided on how to close them, but without taking into account possible exploitation of these vulnerabilities.
Typically, vulnerability scans are performed by proven commercial products such as ImmuniWeb Discovery, an award-winning OSINT technology with artificial intelligence which generates a report with your vulnerabilities found and recommendations for remediating them.
In general, along with open source penetration testing, even individually, these programs are effective. If you use at least one tool from each category, you will provide a comprehensive analysis of vulnerabilities and thereby increase the level of information security. It should be remembered that network scans must be performed regularly, and especially either after any changes to the infrastructure.
| ImmuniWeb® Discovery reduces complexity and costs of cybersecurity compliance via continuous discovery of your external digital assets and attack surface enhanced with proactive dark web monitoring. Learn more with ImmuniWeb Discovery |  |
What’s Next?
- Learn more about ImmuniWeb Community Edition
- Explore other 20 use cases how ImmuniWeb can help
- Follow ImmuniWeb on Twitter, LinkedIn and Telegram
- See the benefits of our partner program
- Request a demo, quote or special price
- Join our upcoming webinars
- Subscribe to our newsletter


