Cybersecurity Compliance: How to Enforce it in 8 Easy Steps
Cybersecurity compliance is a necessary activity for an organization because of a number of
international and local laws and regulations which may impose severe sanctions
and fines in case of non-compliance.
Cybersecurity compliance has become one of the most important aspects of any company's life. Businesses are actively considering the best practices and concepts for cybersecurity, that would help solve tasks related to risk management.
The Internet is constantly evolving and expanding thus improving the quality of interaction among people and companies around the world. With the spread of public open Wi-Fi networks, we got the possibility to be in touch almost always and everywhere, but such openness requires increased attention to cybersecurity compliance services, since devices connected to open networks can be vulnerable.
Want to have an in-depth understanding of all modern aspects of Cybersecurity Compliance? Read carefully this article and bookmark it to get back later, we regularly update this page.
| ImmuniWeb can help stay compliant with applicable cybersecurity laws and regulations. Learn more about cybersecurity compliance services with ImmuniWeb |  |
What Is Cybersecurity Compliance?
Cybersecurity compliance is the process of adhering to specific laws, regulations, and industry standards designed to protect sensitive information and systems from cyber threats. It involves implementing security controls, policies, and procedures to ensure an organization's security measures meet regulatory requirements.
Key aspects of cybersecurity compliance include:
- Adherence to laws and regulations: This involves understanding and following specific regulations related to data privacy, security, and industry-specific requirements.
- Implementation of security controls: This includes implementing technical, administrative, and physical safeguards to protect sensitive information, such as firewalls, encryption, access controls, and employee training.
- Risk assessment and management: This involves identifying and assessing potential risks to an organization's security and implementing measures to mitigate them.
- Continuous monitoring and improvement: This involves regularly reviewing and updating security measures to address evolving threats and ensure ongoing compliance.
Common cybersecurity compliance frameworks and standards include:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- ISO 27001 international standard
- NIST Cybersecurity Framework
- Other laws and standards
By adhering to cybersecurity compliance standards, organizations can protect their sensitive information, reduce the risk of data breaches, and maintain the trust of their customers and stakeholders.
Free DemoWhy Cybersecurity Compliance Is a Must
Cybersecurity is a prerequisite for the development of the information society. The target for a cyberattack can be both individuals and businesses with money or data that can be of any value. For businesses, protecting information is just as important as for governments protecting their secrets.
It doesn’t matter what type of business your company is engaged in - technological, banking, medical or fast-food services, if you sell something, then a lot of personal data is stored in your network. Your business’s digital assets need protection around the clock no less than physical assets or bank deposits.
Research by ImmuniWeb shows that millions of stolen corporate credentials are available in the Dark Web and exploited by cybercriminals for spear-phishing and password re-use attacks against the largest global companies.
Therefore, cybersecurity compliance services are especially important for companies, since both ordinary thieves and dishonest competitors who resort to hacker services can take advantage of vulnerabilities.
In addition to the dangers to your business and company assets all companies must use cybersecurity and confidentiality compliance mechanisms when collecting or processing user personal information to comply with various regulations. For example, the EU's General Data Protection Regulation or GDPR which came into force several years ago has already become a nightmare for European business owners.
GDPR is not the only regulation. Such compliances and regulations are adopted in many countries all over the world. And in order to meet all these requirements you should enforce your cybersecurity compliance services. Here are the most common ways to do it.
| ImmuniWeb can help your organization meet emerging cybersecurity compliance requirements such as GDPR, PCIDSS, and many others in a simple, agile, and cost-effective manner. Learn more about cybersecurity compliance services with ImmuniWeb |  |
Types of Data Subject to Cybersecurity Compliance
Cybersecurity compliance mandates often focus on protecting sensitive data. Here are some common types of data that are typically subject to strict compliance regulations:
Personally Identifiable Information (PII)
- Name: Full name, including aliases or nicknames.
- Contact Information: Address, phone number, email address.
- Identifiers: Social Security number, driver's license number, passport number.
- Financial Information: Credit card numbers, bank account details, investment information.
- Health Information: Medical records, health insurance details.
- Biometric Data: Fingerprints, facial recognition data, iris scans.
Protected Health Information (PHI)
This is a subset of PII that specifically relates to health information. It includes:
- Medical History: Diagnosis, symptoms, treatments.
- Insurance Information: Health insurance plan details.
- Provider Information: Names of doctors, hospitals, and other healthcare providers.
Payment Card Industry Data (PCI DSS)
This data is specifically protected by the Payment Card Industry Data Security Standard (PCI DSS). It includes:
- Cardholder Data: Credit card number, expiration date, security code (CVV).
- Track Data: Magnetic stripe data from a credit card.
Other Sensitive Data
- Trade Secrets: Proprietary business information.
- Intellectual Property: Patents, copyrights, trademarks.
- Government Data: Classified or sensitive government information.
Depending on the jurisdiction and industry, various regulations govern the protection of these data types. By understanding the types of data that are subject to cybersecurity compliance and implementing appropriate measures, organizations can protect sensitive information and mitigate risks.
Free DemoCybersecurity Compliance Regulations and Standards Across Regions
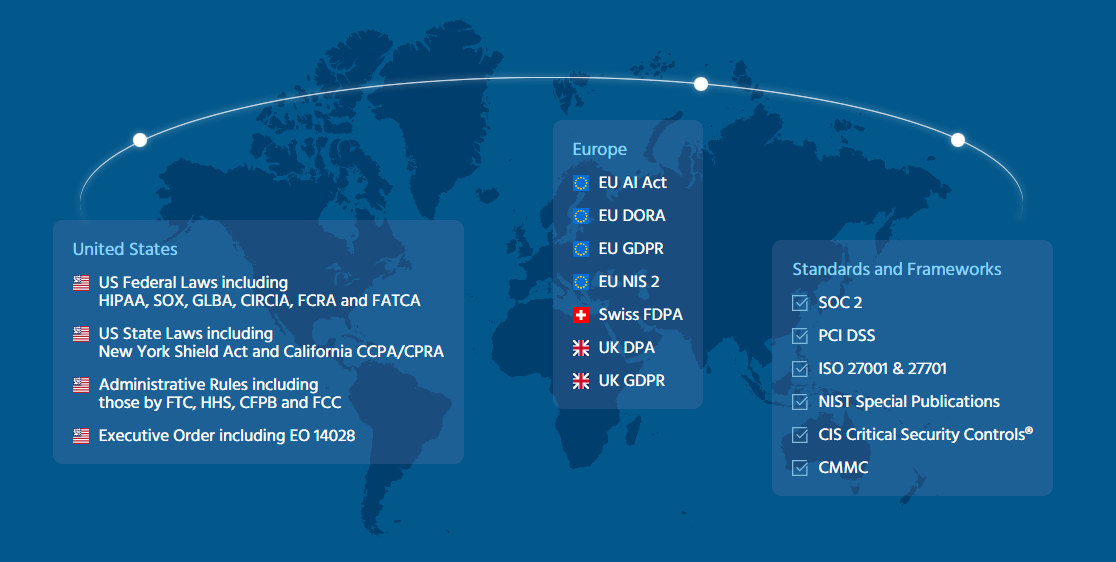
Europe
EU AI Act
The EU AI Act is a groundbreaking piece of legislation aimed at regulating artificial intelligence (AI) within the European Union. It aims to establish a framework that promotes ethical and trustworthy AI while fostering innovation.
EU DORA
The Digital Operational Resilience Act (DORA) is a piece of European Union (EU) legislation aimed at strengthening the operational resilience of financial institutions. It sets out requirements for these institutions to manage and mitigate risks related to disruptions in their IT systems and operations.
EU GDPR
The General Data Protection Regulation (GDPR) is a comprehensive European Union (EU) law that regulates the processing of personal data within the EU. It aims to protect the privacy and rights of individuals with respect to their personal data.
EU NIS 2
The Network and Information Systems Directive 2 (NIS 2) is a piece of European Union (EU) legislation aimed at strengthening the cybersecurity resilience of essential services. It establishes common cybersecurity requirements for operators of essential services across the EU.
Swiss FDPA
The Federal Data Protection Act (FDPA) is a Swiss law that regulates the processing of personal data within Switzerland. It aims to protect the privacy and rights of individuals with respect to their personal data.
UK DPA
The Data Protection Act (DPA) is a UK law that regulates the processing of personal data within the UK. It aims to protect the privacy and rights of individuals with respect to their personal data.
UK GDPR
The UK GDPR is no longer directly applicable to the UK since it left the European Union. However, the UK has enacted its own data protection law, the Data Protection Act 2018 (DPA), which is very similar to the GDPR. The DPA maintains a high level of data protection and ensures that individuals' rights are protected.
USA
In US the following laws and rules apply:
- US Federal Laws including HIPAA, SOX, GLBA, CIRCIA, FCRA and FATCA
- US State Laws including New York Shield Act and California CCPA/CPRA
- Administrative Rules including those by FTC, HHS, CFPB and FCC
- Executive Order including EO 14028
Let’s have a glimpse on some of the most important laws and regulations in the United States.
HIPAA
HIPAA stands for the Health Insurance Portability and Accountability Act. It is a U.S. federal law that sets standards for the privacy and security of personal health information (PHI).
SOX
SOX stands for the Sarbanes-Oxley Act of 2002. It is a U.S. federal law that was enacted in response to a series of corporate scandals, most notably those involving Enron and WorldCom.
GLBA
GLBA stands for the Gramm-Leach-Bliley Act. It is a U.S. federal law that regulates the financial services industry.
FATCA
FATCA stands for the Foreign Account Tax Compliance Act. It is a U.S. federal law that requires U.S. taxpayers to report their foreign financial assets to the Internal Revenue Service (IRS).
New York Shield Act
The New York Shield Act is a law that protects journalists' confidential sources in New York State. It provides journalists with a qualified privilege to protect the identity of their sources, making it more difficult for law enforcement or others to compel them to reveal their sources.
California CCPA
CCPA stands for the California Consumer Privacy Act. It is a California law that gives consumers more control over their personal information.
International
SOC 2
SOC 2 stands for Service Organization Control 2. It is a standard developed by the American Institute of Certified Public Accountants (AICPA) that assesses the security, availability, processing integrity, confidentiality, and privacy of a service organization's systems and processes.
PCI DSS
PCI DSS stands for Payment Card Industry Data Security Standard. It is a set of security requirements designed to protect cardholder data.
ISO 27001 & 27701
ISO 27001 and ISO 27701 are international standards that provide a framework for information security management systems (ISMS).
NIST Special Publications
NIST Special Publications are a series of technical documents published by the National Institute of Standards and Technology (NIST), a non-regulatory federal agency within the U.S. Department of Commerce. These publications cover a wide range of topics related to science, technology, engineering, and standards.
CIS Critical Security Controls®
The CIS Critical Security Controls® are a set of prioritized cybersecurity best practices developed by the Center for Internet Security (CIS). They are designed to help organizations of all sizes protect their systems and data from common cyber threats.
CMMC
CMMC stands for Cybersecurity Maturity Model Certification. It is a cybersecurity framework developed by the U.S. Department of Defense (DoD) to assess the cybersecurity capabilities of defense contractors and subcontractors.
In addition to the laws listed above, there are many other local laws and regulations, including:
| ImmuniWeb can help stay compliant with applicable cybersecurity laws and regulations. Learn more about cybersecurity compliance services with ImmuniWeb |  |
Enforce Cybersecurity Compliance
Be careful what you publish
Enforcing your company's cybersecurity compliance begins with personal information security. Watch and carefully filter what information you disseminate on the Internet about yourself and your company. By sharing the "wrong" information, you can attract the attention of criminals of all stripes and become vulnerable to theft or hacking. Attackers can track what you say on the Internet in your social nets and use it to their own advantage. Do disclose any information about yourself, your brand, your colleges, your products, unless you are absolutely sure that it will not be used against you.
Make sure that the data your company collects is well protected
In order to keep your business data safe, you should conduct an audit and determine which of it is public information and do not require careful protection, which data is of medium importance and its leakage will not affect the business much, and at the end which data is the most important and confidential. The latter category of data will greatly affect the business in case of theft, so it needs to be protected as reliably as possible with the strictest access rights for employees and partners.
Enable HTTPS for your website
To activate HTTPS, an SSL / TLS certificate is installed on the server. This certificate encrypts all data between the browser and the server, whether it’s personal or financial information that is entered on the web page, or the contents of the pages. So, the information is protected from third parties, for example, intruders or surveillance.
SSL certificates can also link your brand to a website This allows visitors to make sure that your website really belongs to your company, but not to a scammer in the case of a phishing site. The EV SSL certificate clearly demonstrates this by coloring the address bar of the browser in green and showing the name of your company.
Use the opportunity to test SSL for free to ensure your cybersecurity.
Use strong and unique passwords
Many Dark Web hackers sell the data that they managed to obtain, including information about millions of users and their passwords. Do not use the same password on different accounts. It vastly increases chances to be hacked. Hackers can pick up your passwords using brute force. It is much more difficult if the password is long, composed of various characters and does not contain words from the dictionary. Use some password manager to remember unique passwords for each service.
Use several authentication factors
Authentication is the act of verifying the identity of a user or device before allowing access to the system. This is done by comparing the provided credentials with an existing database of authorized users, for example, entering a username and password to access an email account. But instead of relying solely on passwords, which are becoming increasingly insecure, we recommend using several factors authentication. Among these factors, a user's specific secret, for example, the answer to a secret question, a digital certificate, a smart card, or a biometric data, such as a fingerprint.
Update all software
Hackers are always looking for new vulnerabilities in the software that you use. Finding them is as easy as finding a path on your Windows network. At the same time, software companies themselves are working hard to release patches to fix these vulnerabilities, so it is very important to update the software as soon as the update is released.
Back up all data
Backups ensure that in case of data loss, files can be restored. You should always store data in different locations physically spaced to ensure cybersecurity compliance, since hackers will not be able to access everything at once. Remember that backups need to be updated regularly.
Install a firewall on the Internet gateway
Firewalls are designed to prevent unauthorized access to a private network. You can establish a set of rules to determine which traffic is allowed and which is prohibited. A good firewall should monitor both inbound and outbound traffic.
| ImmuniWeb® Discovery reduces complexity and costs of cybersecurity compliance via continuous discovery of your external digital assets and attack surface enhanced with proactive dark web monitoring. Learn more with ImmuniWeb Discovery |  |
Use Basic Cybersecurity Compliance Rules in Your Company
Typically, recommendations on cybersecurity compliance for companies are prescribed and mandatory for acknowledging and implementation by employees of the organization who use devices with the ability to access the Internet. The list of these rules may vary slightly depending on the company, but often it consists of several basic recommendations to keep the cybersecurity of the company at a high level:
- the use of complex passwords with their regular change;
- a ban on opening and launching unknown files;
- a ban on downloading and installing new software for the implementation of which they use an admin password on all devices on the corporate network;
- a ban on opening e-mail from unknown and suspicious addresses;
- private access to internal files of the system, using exclusively corporate mail to transfer access to them;
- limited user access to projects of a different level. Each employee has access exclusively to the projects that he or she needs to work;
- a ban on the use of removable digital storage devices;
- use of licensed software.
These measures are basic, but when implemented, are sufficiently effective to ensure the cybersecurity compliance of the company. Of course, they themselves do not protect against hacker attacks on the company’s network, but they leave much less chances for their successful conduct.
You can check your website right now for GDPR and PCIDSS compliance using ImmuniWeb Website Security Free Test.
| ImmuniWeb can help stay compliant with applicable cybersecurity laws and regulations. Learn more about cybersecurity compliance services with ImmuniWeb |  |
What’s Next?
- Learn more about Cybersecurity compliance services with ImmuniWeb
- Explore other 20 use cases how ImmuniWeb can help
- Follow ImmuniWeb on Twitter, LinkedIn and Telegram
- See the benefits of our partner program
- Request a demo, quote or special price
- Join our upcoming webinars
- Subscribe to our newsletter


